Thursday, December 31, 2015
Friday, December 18, 2015
Increase Internal Memory of Your Android Phone
Increase Internal Memory of Your Android Phone
You know that the most important part of an Android phone is the internal memory. Because it installs every app. This internal memory is not a big problem for those who have a high-end phone with a lot of good money because their internal memory is like 8Gb, 16GB, 32GB but most of the low-end phones use it so this internal memory is very deep 1GB, 2GB, 4GB is like this, so we have less space for apps with knee-jerk music films. Finally, when we go to install apps, we say there is not enough memory. So let me tell you about a way to increase it. But for this, you need to have your phone rooted. Go here to see how to root.
There are two ways to increase internal memory.
1st method
By Partitioning a Memory Card (Partition Memory Card):
What we are actually doing is allocating some space from our memory card. Together we need a partition software and an app called Link2SD. With this app, we can install as many apps as we like.
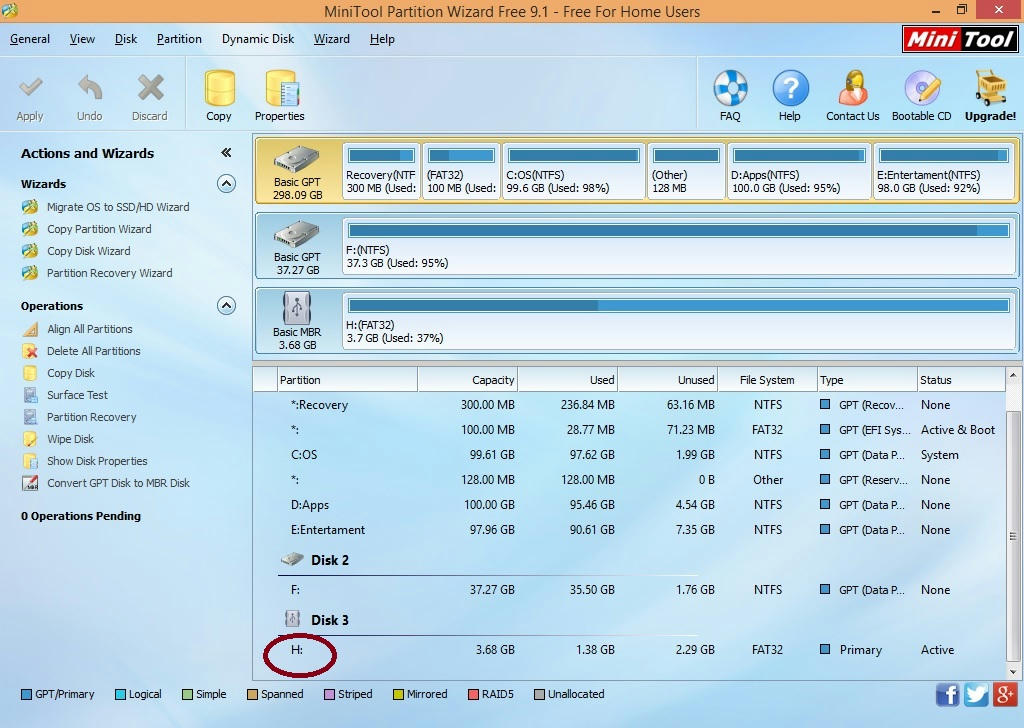
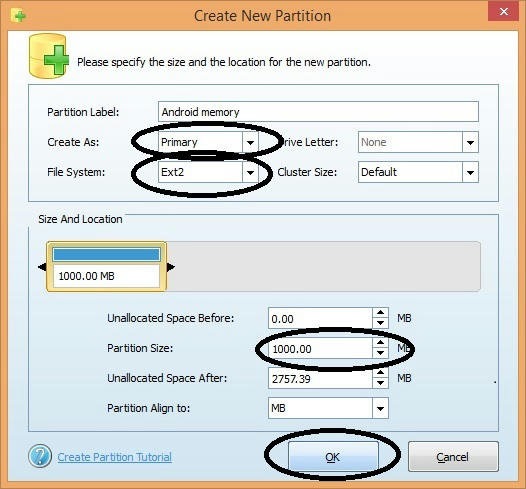
1. First you need to download a Partition Wizard Manager. Download the one you like.
2. Connect your memory card to the computer with a card reader
3. Make a backup of the data on your SD card.
4. Now install the downloaded tool and open the memory card
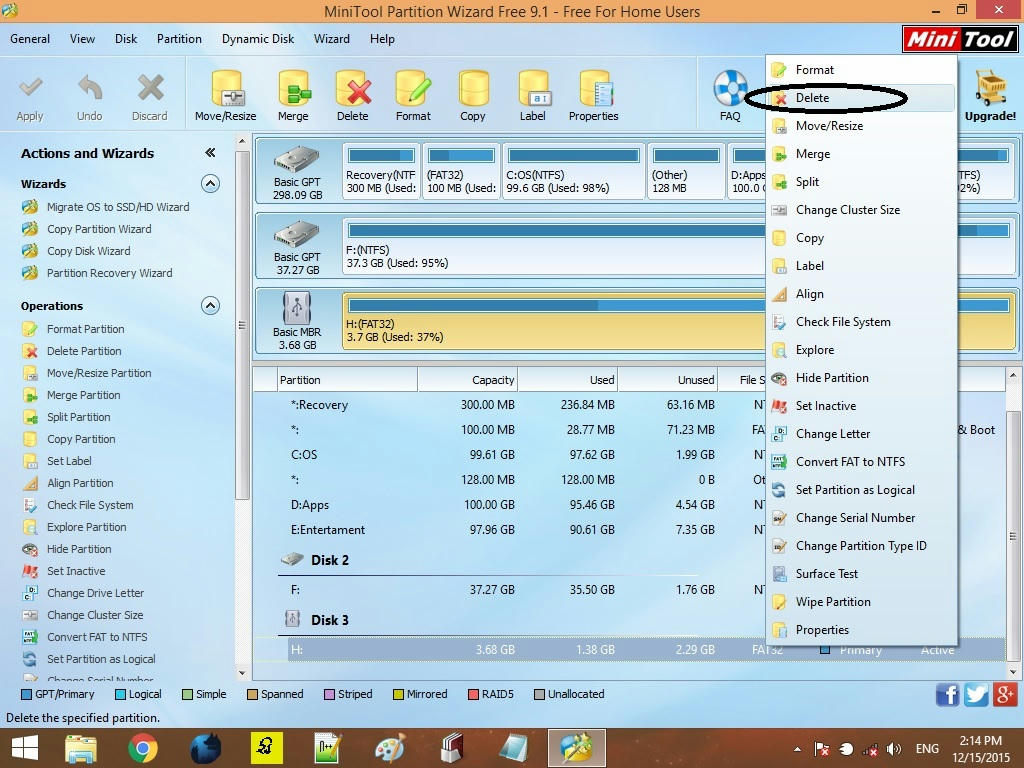
5. Now right-click where your memory card is displayed and give the option "delete".
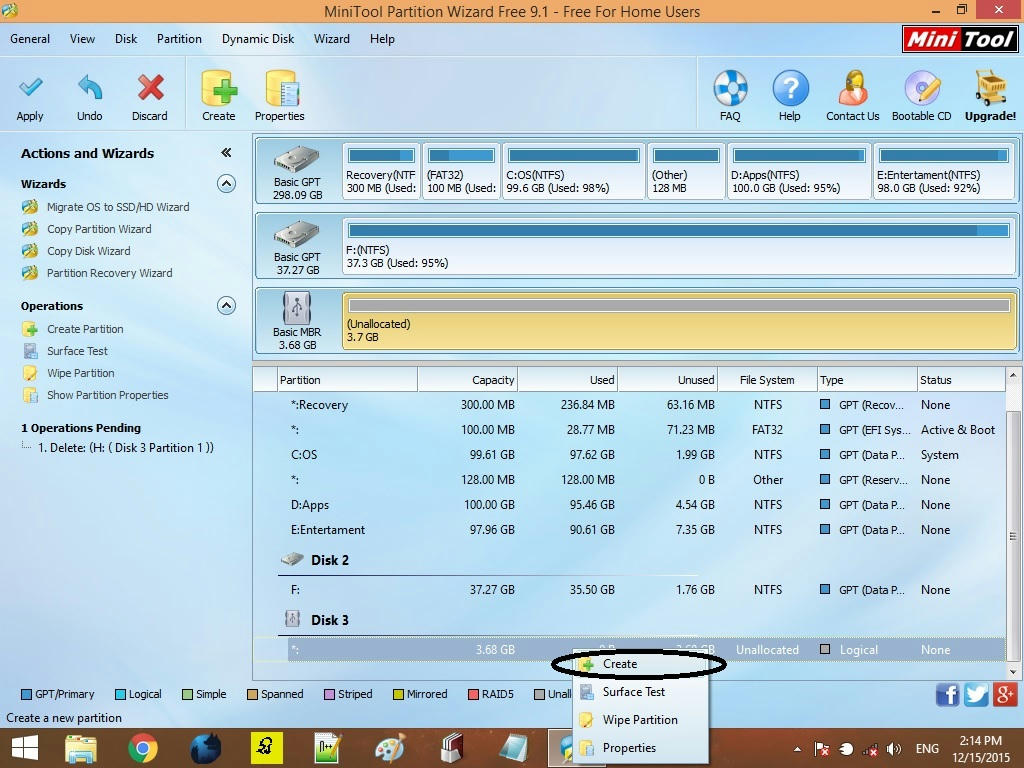
7. Then do one "Create as Primary".
8. Then go to the previous one and give the desired memory to your phone memory as ext2 / ext3 / ext4 as one of these. Give ext2 to anybody because most phones support this.
9. Give it a “Create as the primary” (both the partitions we created must be primary or this will not work).
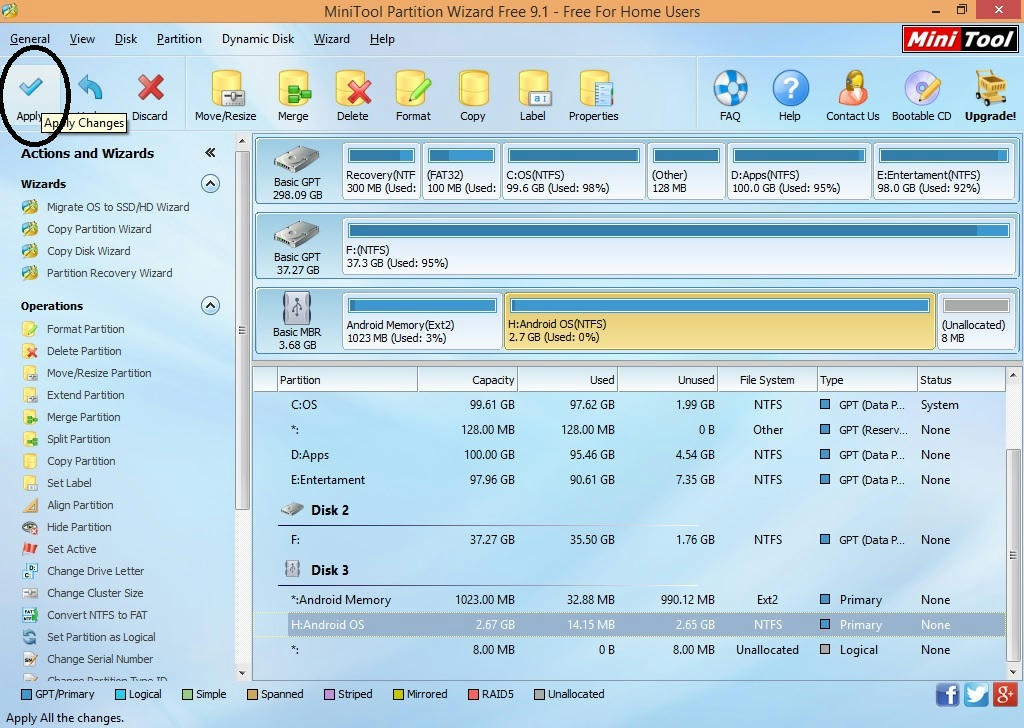
10. Now work or then give you're "apply" and then work right now 2 partitions have been created. Remember, you are now shown only the partition that was previously made of "FAT32".
Right now the first way is over
2nd method
In this case, you need to have ClockwordMod installed on your phone or you can not do this without your phone. If you have CWM, you can choose the one you like and work with it. I do not know the name of this. I do not know what to do with it. I do not know what to do with it.
Let's see how to use Link2SD
1. You have now partitioned the memory card, then download this app now
2. Now insert the memory card into the phone and open the app
3. Then the box will ask you what is the format of your second partition and give it the ext2 / ext3 / ext4 you gave earlier. If you gave ext2, select one.
Then it says Mount Script Created and then reboot your phone. Then open the app again and if no message comes then it will work. Then you can click on the apps that you have on your phone and tick the ones at the bottom of the menu (app, Dalvik-cache, and library files). You can not put a tik together. You have to pay for that app together.
4. Then type "create a link".
5. Now look at the Storage Info and then you can see your storage info. Send it to your previous memory and the new one.
6 . Okay now you know as much as you can about the newly created part of the app.
So today is the end of the article. Don't forget to like, comment and share...
Wednesday, December 16, 2015
How to root my android phone
One of the questions most people who buy a new Android phone ask is "Should I root the phone or not".
Most Android phones have basic settings that the user can use with some restrictions. That means we can't do a lot of things related to the system. Rooting will cause you to lose all of these boundaries. That means we can add a lot of new work to our Android system.
Is it dangerous to root the phone?
I was too scared to root at first. But somehow finally rooted. Many people are afraid that their phones will be broken. But it is much less likely to break during rooting
Why root the phone?
Simply put, you can take full control of the phone. (I wanted to put Sinhala. I want to increase my memory.)
Advantages of rooting
1. Rooting removes the limitations of using an Android OS.
2. You can install unofficial Android versions (custom ROM). Some phones do not receive official updates on the latest versions of Android. You can then install a new version using a custom ROM. The phone must be rooted for this.
3. Some phones need to be rooted to take screenshots.
4. Ability to use Sinhala language. (For me, this is the biggest advantage).
5. Apps are installed on the phone's internal memory. You can install these apps on the SD card by rooting. (For me, this is the second biggest advantage).
6. The processor can be over-locked / under-locked.
7. In addition, there are many other benefits.
Disadvantages
1. Rooting some phones will not be able to make an official update.
2. Rooting can slow down the phone.
3. If rooting is not done properly, the phone may be Unusual things can happen.
Finally, I have to say. Rooting will void the warranty of the phone, and if you are new to Android, this is a bit risky. Therefore, rooting should be done very carefully. There are different ways to root each phone. And you can unroot it if you like.
Okay now let's see how to do it
- Go Here here and get that APP.
- Install the app.
- Then in the menu that appears, give the root.
Give install superSU first and then Gandalf.
All right, now reboot your phone. Then see if there is a superSU in your apps that is rooted.
So today is the end of the article. Don't forget to like, comment and share...
Monday, December 14, 2015
Shall we learn Java?
There are many people who love to learn Java, I brought this to them. I wanted to publish this in parts, but these days I'm going to give it a pdf because my net connection is going down. Now let's see what Java is,
Java is currently the most popular programming program in the world. Java is the most widely used programming language for creating beautiful web pages, writing various programs for smartphones and PDA devices. Even a person with no basic knowledge of the Java programming language can learn through this series of lessons. This tutorial also includes tips for those who are currently working in Java.
Click this image to download
Ah, I put this in our forum, I thought I could not edit it again, so I put it like that.
So today is the end of the article. Don't forget to like, comment and share...
Thursday, December 10, 2015
Anonymous declare December 11 as ISIS ‘Trolling Day’ and you can be a part of it
It's been a long day. It's too much work these days. It's 10 o'clock now. What I saw by chance is that you know that after the ISIS attack on Paris (after the anonymous deadly terrorist attack in Paris) Anonymous declared war on ISIS. In the past, their FB, Twitter, accounts were blocked, but now they are doing the same thing to their site as if they were hitting DDoS. They ask us to make fun of ISIS 'banners, posters, videos, images and edit them. I didn't do it,
Following the Paris attacks, the collective known as Anonymous launched a campaign against ISIS and its supporters. They have also taken down various social media accounts of the organization. They also launched attacks on ISIS' propaganda websites.On December 11, the hacker group called Anonymous declared that it would expose the evils of the Islamic State through various means, including by releasing satirical images and videos of the group.In a nutshell, Anonymous’ goal was to spread fear about ISIS among the Western-living Muslims who are falling for the organization’s silly social media propaganda.The campaign started on a 4Chan thread and slowly gained the attention of ordinary Internet users. Next Friday, the hackers behind the project will try to fill the Internet with their own art.
FOR MORE DETAILS CLICK HERE.
So today is the end of the article. Don't forget to like, comment and share...
The Top Ten Hacker Tools of 2015
The Top Ten Hacker Tools of 2015
You must know the name of a hacker tool because if you do not know about it, you can be hacked. But do not be afraid because we are together.
These are the top ten hacker tools this year.
1. Nmap: Network mapper
Nmap is a multi-purpose tool for abbreviated network security, free and open-source (free and open-source), often used by network administrators for network detection and security auditing. System administrators use the Nmap to determine the open port, network inventory, managing service upgrade schedules, and host monitoring (this is used for computers on the network) or services.
2. Metasploit:
A tool used to find vulnerabilities on the network. This tool is either free or open-source. This Metasploit project is very popular and used by pentesting or cybersecurity professionals and hackers. Metasploit is a computer security project that helps set up knowledge and skills testing and buyer testing that provides in-depth information on known security vulnerabilities.
3. Cain and Abel:
Cain and Abel is the password recovery tool most commonly used for Microsoft operating systems. This public eavesdropping tool (CA) secretly obtains passwords used to make calls using the Internet. Cain and Abel are the best password recovery tools currently available.
4. Angry IP Scanner:
Angry IP Scanner is popularly known as 'IP-scan'. It is open-source and cross-platform. It scans the network and is fast and easy to use. This is usually used by network administrators and system engineers.
5. John The Ripper:
This is a commonly used password cracking tool. This is done by taking samples of different passwords and matching them. John the Ripper is free and Open Source software, distributed primarily in source code form. If you would rather use a commercial product, please consider John the Ripper Pro, which is distributed primarily in the form of "native" packages for the target operating systems and in general is meant to be easier to install and use while delivering optimal performance.
6. THC Hydra:
Although often referred to as another password cracker, THC Hydra is very popular and has been developed by a very active and experienced development team. This speeds up hacking network access and obtaining passwords. This includes the mail protocol (POP3, IMAP, etc.), Databases, LDAP (Lightweight Directory Access Protocol), SMB, VNC, and SSH (Secure Shell, used by VPN Software). Supports
7. Burp Suite:
Burp Suite Professional is one of the most popular penetration testing and vulnerability finder tools and is often used for checking web application security. “Burp,” as it is commonly known, is a proxy-based tool used to evaluate the security of web-based applications and do hands-on testing.
8. Nessus Remote Security Scanner
Source has recently been shut down but is still available for free. Works with a client-server framework. Nessus Remote Security Scanner is the most popular insecurity status scanner. Nessus is used by over 75,000 organizations worldwide for business purposes.
9. Ettercap:
Ettercap is used by many cyber security professionals. It works by connecting the user network interface to the ARP (ARP: Address resolution protocol) and working with the MAC address (address of its Network Interface Card) knowing the IP address. Provides IP addresses.
10. Wapiti:
It works as a scanner. It scans all the information in the computer "black-box" scans the HTML application, scripts, forms, etc. on the web pages. This is a multi-purpose hacker tool.
So I told you about The Top Ten Hacker Tools of 2015, so today is the end of the article. Don't forget to like, comment and share...
Wednesday, December 9, 2015
About Torrent
About Torrent
This is God for me. Because all the software that has been cracked is available from this and all the movies and TV serials are downloaded from this.
Torrent means "stream". Torrent is actually a very successful design. You will understand why at the end of this article.
Let's first see how to download a movie from a torrent.
1. First you need torrent client software to download a torrent. There is a lot of software for this, but this is the best.
All of this software is free and very small. Download the one you like. We only recommend uTorrent and BitTorrent .
2. Install the downloaded software on your computer.
3. Now select the movie you want.
4..In every article that has a link to download the movie..go to that link.
5. Download the "torrent file" from that link to a place where you can use it easily.
6. Now right click on the downloaded file and select Open with the software you installed earlier.
7. Now the software will ask you for advice on where to save the movie.
The movie will now download according to the speed of your internet connection.
The technical side of torrents.
- What a torrent file!
- What Is a torrent client!
- What Is a torrent tracker!
- ටොරන්ට් ක්රියාත්මක වෙන්නෙ කොහොමද?
This is how a torrent works. Suppose X has a new movie and he wants to share it with others. He can create a torrent file. Create and give that file to Z. Then Z will start downloading it through its torrent software. X did not upload this movie anywhere. When you download Z, this torrent goes from X's computer. This action is managed by a tracker. So X has to upload this movie until Z is finished, this is what is called seeding. Now Z also has the relevant movie. This is the basic theory.
Now let's see what happens to the most famous movies.
Here a person uploads a torrent file (not a movie) to a torrent distribution website (now Cedars 1). Suppose 10 people searching for this movie see this torrent. They download it and upload it while downloading. It also downloads the movie. (Now there are 10 Cedars) Here are 100 more people who will see and download this torrent and upload it immediately. (Now Cedars are 100+) This is how the popular movies we download come to our computers.
This means that the movie came to your computer through someone else. The seed for a while after downloading the movie and help someone like you.
If you watch this video. Video, you will understand betterIf the seeds in torrents are low...
One of the problems with torrents is that they slow down when the seed is low. So let me give you a little solution. But this may not be 100% right.
♦ In uTorrent, double-click or right-click the torrent to open the Properties window.
♦ In the box labeled "trackers (separate tiers with an empty line)" there is a list of trackers of the relevant torrent.
So now all you have to do is copy the trackers here and paste them at the bottom of the box. (You need to keep a line spacing between trackers)
♦ Do not delete existing trackers.
♦ Then click OK.
♦ Watch this Video to know more.
Download Torrent Direct.
You can use the following websites to download torrents directly from a torrent client (eg: IDM, JDownloader). Follow the instructions on those sites.So today is the end of the article. Don't forget to like, comment and share...
Sherlock
Sherlock Holmes, as you say, reminds you of the great detective of the 1890s. You may have read and seen all about his exploits. Just think, if Sherlock Holmes had lived in a modern age like 2010, how would he have solved this mystery? That's very interesting, isn't it? If you want to lose that curiosity and count, you have to look at this. A great detective story that you can enjoy without any fear, I invite everyone to watch this and leave a little comment.
Let me tell you a little bit about this design. This is a series that has been airing on television in the UK since 2010. There are five stories in this series. We will be able to see it all in the future. This design has a high IMDb rating of 9.3. Also, Benedict Cumberbatch, a well-known actor, will play the role of Sherlock Holmes. He's a contributor to famous movies like Tinker Tailor Soldier Spy. Dr. Watson is played by Martin Freeman. You can see their prowess in this production. However, this is full of curiosity. I'm looking forward to season 04 because there's a story that the next piece will be even more interesting. How can a dead person return?
Watch the trailer
Extra details Wikipedia Download
First episode date: July 25, 2010
Genre: Crime; Mystery; Comedy-drama
So today is the end of the article. Don't forget to like, comment and share...
Tuesday, December 8, 2015
The 100
the 100 [2014]
Extra details Wikipedia Download
An empty world devastated by a nuclear war. A lifesaver living in interconnected orbiting space stations. The penalty for all crimes in a life devoid of resources is death. At the age of 97, 100 young criminals are sent to Earth to see if they are fit to live. But what has the earth become like after this tragedy? Does the beauty seen from the sky stay there? Will these young criminals, who have never lived on earth, be able to survive?
Currently, 02 seasons have been telecast and the 3rd season is coming soon.
The IMDb rating here is 7.8 / 1070,867 votes.
Original release: March 19, 2014 –; September 30, 2020
So today is the end of the article. Don't forget to like, comment and share...
Legend of the Seeker
"The Legend of the Seeker" or "The Legend of the Seeker" is based on the novel "The Sword of Truth" by Terry Goodkind. This is a novel that has become very popular all over the world. Details about the novel are here.
The Legend of the Seeker series, which is rated 7.5 / 10 on the IMDb, is full of magic, adventure and love. Craig Horner as Richard Cypher or Seeker for the Legend of the Seeker series filmed in beautiful New Zealand, Bridget Regan as Kahlan Amnell or Confessor as Zeddicus Zu'l Zorander or Bruce Spence as Craig Park as First Class Wizard. Joining the play.
Now we turn the story aside. When people are oppressed and helpless, a hero stands up for those people to fight against evil. He calls himself Seeker or Seeker. At this time, people are very helpless because of the evil ruler called Darken Rahl. Meanwhile, a rabbi prophesies on the verge of death about the Seeker. That Seeker's birth took place in a city called Brindington. So Darken Rahl sends his D'Haran army to kill every firstborn child in the city. But a sorcerer named Zed takes the real Seeker and escapes to Heartland. Years later, at the appointed time, Ceylon's confessor finds Seeker and returns to Hartland. Richard Cypher still does not know that he is the Seeker of this prophecy. Zed didn't even tell him. So Richard does not accept this story at all. Richard, who must wield the sword of powerful truth, has to explain his destiny to Caylan. What will Richard, Ceylon, and Zed do next? How do they prepare to destroy the Dark Rahl? Let's download the story and see, shall we?
Watch the trailer
So today is the end of the article. Don't forget to like, comment and share...
REVOLUTION
People living in a country where governments were overthrown on fear, confusion, and panic after the collapse of the electronic world on which everything depended.
An attempt by a family led by the group caused the power outage to restore power.
A leader who owns electricity only for himself and prepares to conquer other republics. A group of rebels break away from him and fight to defeat him.
This is the story of a power struggle in a world without electricity.
The story begins with the sudden shutdown of all energy sources on earth, including electricity. In short, even batteries. You know how messy it is to go without electricity. What's more, even the engines of all vehicles become inoperative. In short, people are going back to the stone. Governments collapse and the strong control the weak. But one man knows this in advance and takes a program to a pen drive. His brother is an Army soldier. What's that secret? Will the earth return from the Stone Age? Who is the leader of the army chasing that secret? This story, which runs in a completely different way with no shortage of action, has already won the most votes in a TV series with an audience vote on one website.
Original release: September 17, 2012 –; May 21, 2014
Producers: Athena Wickham; Robert M. Williams Jr. Trey Callaway
Production locations: Atlanta, Georgia (Pilot); Wilmington, North Carolina (season 1); Austin, Texas (season 2)
Extra details Wikipedia Download
So today is the end of the article. Don't forget to like, comment and share...
Water Fox Web browser
Water Fox
When you say this, do you not remember our firefox? What is this water fox? You know, our Firefox (brother Fox) is his brother. This is the only thing Firefox does. That means this is a Web browser. But this limitation means that this water fox only works on computers with X64bit installed. This is faster than our firefox. One is the only good one.
Click this image to download
Here I said about a new web browser.
When you say this, do you not remember our firefox? What is this water fox? You know, our Firefox (brother Fox) is his brother. This is the only thing Firefox does. That means this is a Web browser. But this limitation means that this water fox only works on computers with X64bit installed. This is faster than our firefox. One is the only good one.
Click this image to download
Here I said about a new web browser.
So today is the end of the article. Don't forget to like, comment and share...
online Train Tickets From Hutch
The queues at the train station are over ....... take your phone and dial 365 to book train tickets.
To make a reservation, call 365 and call the reservation agent.
This service is available for the following railways
1. Kandy - Colombo Intercity
2. Vavuniya Intercity
3. Vavuniya Night Post
4. Yal Devi
5. Badulla Night Mail
6. Kandyan Gem
7.Podi Manike
8. In the Rajadhani Express luxury cabin
Relevant fees
1. Ticket value + 15% off (17% off Rajadhani Express) +
2. Rupees per minute. 8 + tax will be charged for the call.
In order to provide you with a fast and efficient service you must provide the following information.
1. Make sure you have all the information you need - date, time, route, number of seats ready
2. You will take the necessary steps to add up the total transaction value of your mobile balance to complete the booking.
3. You will receive an sSMS message containing all the information that your reservation was successful.
4. You can use this information from the special counter at the Colombo Fort Railway Station where you collect tickets or from the Colombo, Gampaha, Peradeniya and Kandy Railway Stations
5. The maximum number of questions that can be separated by one hutch number is 5.
6. Tickets can be booked 45 days in advance.
7. Reservations will be canceled 2 hours after the departure time of the train.
Refunds
1.We are not responsible for any cancellation or changes in your itinerary for any cost receipt or for cancellation of itinerary due to train delay
2. Withdrawals should be made in accordance with railway rules and regulations
3. Invalid Advance Station M Seat Reservation System will be operated for at least 24 hours.
Sunday, December 6, 2015
Yakadaya Syndi
Here is the official blog reader made from our hacking forum. This is our ELITE_x work just started. Our Area said let's do this as our Cindy. We have made it one of the official blog readers of our forum. Then read all the blogs Go here or add your blog Click on the image below
So today is the end of the article. Don't forget to like, comment and share...
TEEN WOLF
A lot of people have heard of this. I don't think I need to say anything strange. The fifth season of the story is currently airing. The teen wolf series began airing in 2011. It was telecast on the American channel MTV. But in 1985 there was a movie called Teen Wolf. It is said that there is a slight influence on the film.
So this drama series has won many awards and has been nominated for many awards. So let me tell you a little bit about the story.
This story is about Kenneth Scott McCall. He is a student of higher education. Located in Bacon Hills. But Scott's life changes completely when he is bitten by a human-wolf. That Scott also became a human-wolf. So Scott needs to learn how to control this power, and he also has to control these things because he's more likely to kill people. But day by day his strength increases. This young life is automatically undergoing a big change. Scott, who used to be like Kong Wela, suddenly becomes known to the whole school in a way that no one could have imagined. But Scott is trying to live a normal life. Hide the secret of this human-wolf from everyone. Even from his best friend Styles. But his thinking is changed by another human wolf, Derek Hale.
Those who know a little bit about this do not need to explain this story in a strange way. So watch out then.
The IMDb value here is 7.8 / 1077,454 votes.
First episode date: June 5, 2011
Genre: Teen drama; Horror; Supernatural; Action; Romance
So today is the end of the article. Don't forget to like, comment and share...
Sri Lankan First 3D Car Game (Victory Racing)
Sri Lankan First 3D Car Game (Victory Racing)
Game Created by - P.Madusha Nishad Perera
Excerpted from our forum -www.yakadaya.com
I thought I knew about a game that the cast should play this holiday season. It was made by a boy in our country. To be honest, this is made by a friend of a friend I know but I don't know about it but I wish I could hit more like this. Hmmm, let's get to work now.
This game is the first 3D Sinhala car game created in Sri Lanka. This is a game that supports computers with a small VGA. Not going to say more. If it looks a little messy. That is if you can adjust the settings.
Screenshots
Download [59.38MB]
Tell me if the game is hard to play. Ah ... another maybe the virus guard catches the game setup. It's not because of a virus. It is 100% sure. I checked it out. Because he told me it was something that happened while making that game.
Another thing I said was that my friend would crack the one in that village (the only one his friend didn't hit) and say if it's hard to hit. Made another brand new car (my friend). Tell me if you want them too. Please finish this game first. I'll give it to you later (I haven't even given you the new car set yet).
Game Created by - P.Madusha Nishad Perera
Excerpted from our forum -www.yakadaya.com
So today is the end of the article. Don't forget to like, comment and share...
Always be courteous to contact us If you want any help.